Whoa, seriously, this is weird. I installed a Solana wallet extension last week to test its UX. My first impression was slick and familiar, like a polished app I’ve used. But somethin’ felt off about the permissions dialog, and my instinct said I should pause, check the origins, and think twice before importing anything like seed phrases or wallets. So I dug deeper, poking around settings, release notes, and the extension’s homepage…
Really, that caught me off guard. Okay, so check this out—there’s Phantom, Glow, and a few small forks competing for attention. I tried Phantom’s extension first because people in the US crypto groups kept recommending it. Initially I thought a popular wallet equaled safety, but then I realized that high download counts and glossy screenshots don’t replace careful vetting, especially when you’re about to authorize contract interactions or sign transactions that move real money. I’ll be honest: the onboarding flow is smooth, but some parts felt ambiguous.
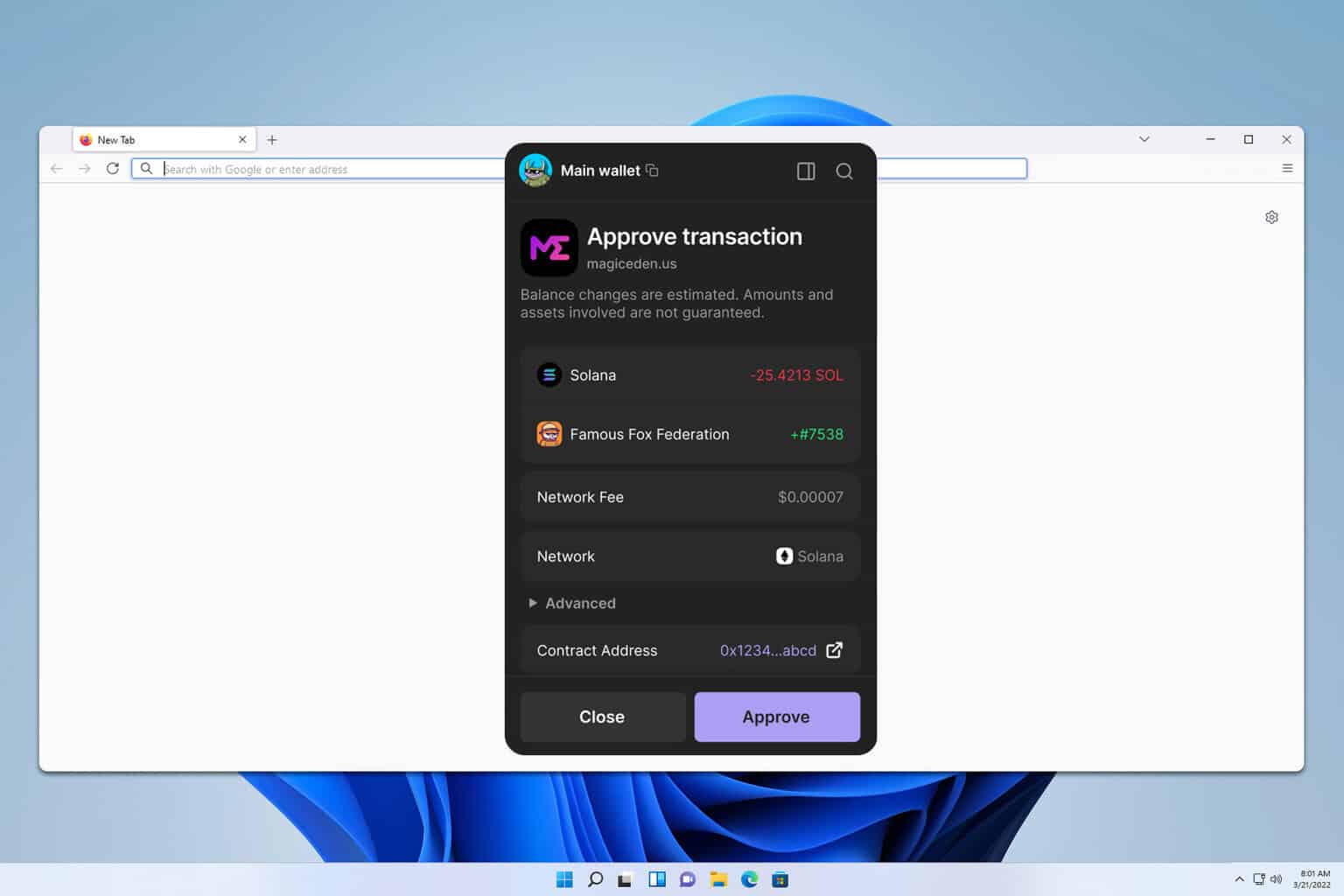
Hmm, I’m a little wary. Here’s what bugs me about permissions: extensions often ask for rights phone apps wouldn’t. Sometimes they request access to all sites or broad storage, and users accept by habit. On one hand it’s intuitive to trust a wallet that looks polished and has a familiar logo, though actually, when you parse the extension’s manifest and its third-party dependencies you might find telemetry hooks or auto-updaters that introduce risk vectors you didn’t consider at first. So I tracked network calls during a test mint to see which endpoints were pinged.
Really, that surprised me. There were calls to CDNs, analytics endpoints, and one unfamiliar domain returning JSON. My instinct said stop and inspect, but I pushed on to the signing step. Initially I thought a failed mint would be harmless, but then I realized that some signatures can authorize program-derived addresses to spend or transfer assets unexpectedly, and the nuance of Solana’s transaction model makes those interactions non-obvious to many users. I’m not 100% sure, but that part bugs me a lot.
Here’s the thing. If you’re comfortable reading manifests and monitoring WebSocket traffic, you can vet an extension properly. Most people aren’t, though, and that’s where curated directories and trusted downloads matter. So here’s my practical rubric: prefer extensions with open-source code you can skim, reproducible builds or verified publishers, minimal, very very limited permissions, clear privacy policies, and an active, responsive team that answers security questions publicly rather than burying them. Also check US community channels for reports of malicious updates or phishing campaigns.
Wow, people really react fast. Okay, so check this out—I’m biased, but I’ve started recommending a staged setup to friends. Install from the verified source, make a throwaway wallet, test small transactions first. When I shared this with a few collectors in NYC they thanked me, though a couple were annoyed (rightfully) that onboarding nudges created by marketing teams emphasize features over risk disclosures, and that mismatch between hype and security posture is something I keep worrying about. If you want a safer start, check official Phantom distribution and community feedback before installing.
Where to get it (and how to verify)
For a straightforward starting point, I link to the official-looking distribution page I referenced during my checks: phantom wallet download extension. Verify the publisher, compare the checksum if they provide one, and cross-check the repo on GitHub (or wherever the team publishes code) before trusting it with NFTs or SOL.
Okay, so a few practical tips because people ask: never paste a seed phrase into a website. Seriously. Use hardware wallets for large holdings. Rotate keys if you suspect any compromise. (Oh, and by the way…) keep small test amounts handy so you learn what a normal flow looks like. My instinct said those small habits cut a lot of avoidable risk.
Common questions
Is Phantom safe for NFTs?
Mostly yes, if you follow basic hygiene: download the extension from an official source, check community feedback, and avoid approving unknown contracts. I’m not 100% certain about every fork, but vetted releases with visible maintainers and reproducible builds are a much better bet than random copies.
How do I check permissions?
Open the extension’s details in your browser, read the manifest, and watch network calls during a test transaction. If the extension asks to access all sites or has strange third-party domains, that’s a red flag. If you’re unsure, pause and ask in a trusted community channel.
What if I already clicked accept?
Change keys and move assets to a fresh wallet if you suspect exposure. Revoke approvals you don’t recognize (wallet UIs and some block explorers let you view and revoke delegations). I’m biased, but doing those steps early can prevent much bigger headaches.